本文摘要:
The article discusses how to block requests to a specific domain, "md.hi.sb," often used by encrypted JS on a website's main page. It provides a JS code snippet that overrides the fetch and createElement functions to prevent unauthorized script loading. Additionally, it recommends adding a Content Security Policy (CSP) meta tag to the HTML header to enhance security. This method effectively stops the external requests without the need for decryption, ensuring cleaner access to the site.
— 本文部分摘要灵感源自 DeepSeek 深度思考 ✨
看到有人在求这个代码,下载看了一眼
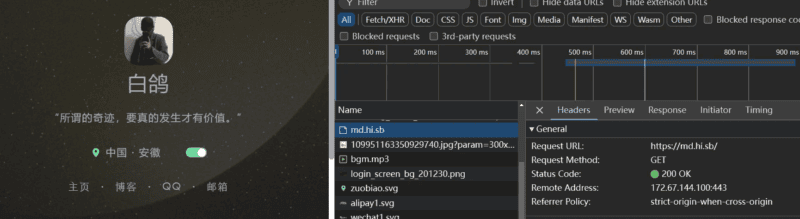
访问主页,加密的 JS 会去请求一个远程地址
![图片[1]|KXD黑-流星个主页–去后门版|不死鸟资源网](https://busi.net/wp-content/uploads/2025/06/20250615055356215-image-1024x280.png)
懒得费事解密了,直接屏蔽之。
新建一个 JS 文件内容如下
(function() {
const originalFetch = window.fetch;
window.fetch = function(url, options) {
if (url.includes('md.hi.sb')) {
console.log('Blocked request to: ' + url);
return Promise.reject('Blocked request to: ' + url);
}
return originalFetch.apply(this, arguments);
};
const originalCreateElement = document.createElement;
document.createElement = function(tagName) {
const element = originalCreateElement.apply(this, arguments);
if (tagName.toLowerCase() === 'script') {
const originalSetAttribute = element.setAttribute;
element.setAttribute = function(attr, value) {
if (attr === 'src' && value.includes('md.hi.sb')) {
console.log('Blocked script from: ' + value);
return;
}
originalSetAttribute.apply(this, arguments);
};
}
return element;
};
})();然后在 index.html 里插入
<script src=”js/1.js” type=”text/javascript”></script>
并在 html 头部加入
<meta http-equiv="Content-Security-Policy" content="default-src 'self' https://cdn.jsdelivr.net; script-src 'self' https://cdn.jsdelivr.net; connect-src 'self' https://cdn.jsdelivr.net; report-uri /csp-violation-endpoint;">再次刷新访问
![图片[2]|KXD黑-流星个主页–去后门版|不死鸟资源网](https://busi.net/wp-content/uploads/2025/06/20250615055425691-image-1024x275.png)
整个世界都清净晒。加密的源码就不发了,网上一搜大把
本站文章部分内容可能来源于网络,仅供大家学习参考,如有侵权,请联系站长📧ommind@qq.com进行删除处理!
THE END